image via google images
The AMPS was designed for voice transmission is a technology that is used to allow data over the same voice channels with a frequency of 800 MHz. The cellular data transfer needs a connection between every end just like a voice session. During this connection the cellular data transmission sends data over the airlink (through a PSTN (Public Switched Telephone Network)) to the remote computer.
For a well cellular phone have been utilize radio signals originally radio performance losses signals because of interference of noise and channel degradation which affect data transmission. Therefore ETC (Enhanced Throughtput Cellular) have been introduced to control data compression, error correction and modulation to provide faster reliable transmission along with MNP(Mircrocom Network Protocol)..
Showing posts with label Data Communications. Show all posts
Showing posts with label Data Communications. Show all posts
Saturday, September 5, 2009
Thursday, September 3, 2009
The Basic Access Method: CSMA/CA
The Distributed Coordination Function essentially Carrier a Sense Multiplying Access with Collision Avoidance mechanism (also known as CSMA/CA). CSMA protocols are one of the most known protocols in the industry, where the most common one is Ethernet which refers to CSMA/CD protocol (CD standing for Collision Detection).
The CSMA protocol works as A station that transmit senses to the medium if the medium is not responding or some other station is transmitting then the medium will continue transmission at a later stage if the medium is sensed free then the station will accept transmission
The following protocol are very effective when the medium is not heavily saturated, because it allows stations to transmit with minimum delay, but there is always a chance that there is another stations transmitting at the same time because of another stations sensed the medium free and decided to transmit (collision).
In this case the collision must be identified so that the MAC layer could retransmit the packet individually and not by the upper layers which may cause significant delay. The Ethernet collision is identified by transmitting stations that goes thought the retransmission stage based on the exponential random backoff algorithm.
These Collision Detecting mechanism are good for wire LAN and cannot be used on WIreless LAN.
So how do we over come this problems.....
The CSMA protocol works as A station that transmit senses to the medium if the medium is not responding or some other station is transmitting then the medium will continue transmission at a later stage if the medium is sensed free then the station will accept transmission
The following protocol are very effective when the medium is not heavily saturated, because it allows stations to transmit with minimum delay, but there is always a chance that there is another stations transmitting at the same time because of another stations sensed the medium free and decided to transmit (collision).
In this case the collision must be identified so that the MAC layer could retransmit the packet individually and not by the upper layers which may cause significant delay. The Ethernet collision is identified by transmitting stations that goes thought the retransmission stage based on the exponential random backoff algorithm.
These Collision Detecting mechanism are good for wire LAN and cannot be used on WIreless LAN.
So how do we over come this problems.....
Sunday, July 5, 2009
Packet capture
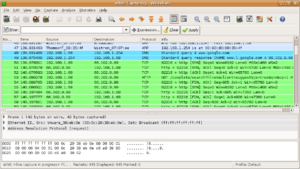 Image via Wikipedia
Image via Wikipedia
This is unfortunate for testing reasons, but fortunate for security reasons. It is fortunate because, if an attacker installs a sniffer in a trusted network, but if the trusted network uses a hub to broadcast the packets within that network, then the sniffer would be able to look at every single packet that is going across the network.
Many network monitoring tools are based on passive packet capture. The principle is
the following: the tool passively captures packets flowing on the network and analyzes
them in order to compute traffic statistics and reports including network protocols being used, communication problems, network security and bandwidth usage. Many network
tools that need to perform packet capture ([tcpdump], [ethereal], [snort]) are based on a popular programming library called libpcap [libpcap] that provides a high level
interface to packet capture.
The main library features are:
• Ability to capture from various network media such as ethernet, serial lines, virtual interfaces.
• Same programming interface on every platform.
• Advanced packet filtering capabilities based on BPF (Berkeley Packet Filtering),
implemented into the OS kernel for better performance.
Depending on the operating system, libpcap implements a virtual device from which
captured packets are read from userspace applications. Despite different platforms
provide the very same API, the libpcap performance varies significantly according to
the platform being used.
On low traffic conditions there is no big difference among the various platforms as all the packets are captured, whereas at high speed1 the situation changes significantly. The following table shows the outcome of some tests performed using a traffic generator [tcpreplay] on a fast host (Dual 1.8 GHz Athlon, 3Com 3c59x ethernet card) that sends packets to a mid-range PC (VIA C3 533 MHz, Intel 100Mbit ethernet card) connected over a 100 Mbit Ethernet switch (Cisco Catalyst 3548 XL) that is used to count the real number of packets sent/received by the hosts3.
The traffic generator reproduces at full speed (~80 Kpps) some traffic that has been captured previously, whereas the capture application is a simple application named pcount based on libpcap that counts and discards, with no further analysis, the captured packets.
Wednesday, June 24, 2009
WFS709TP Wireless Control

The NETGEAR ProSafe Smart Wireless Controller is a full-featured wireless controller that centrally manages 16 access points, delivering integrated wireless mobility, security and converged services for both wired and wireless users.
Supporting up to 256 users per ProSafe Smart Wireless Controller, the WFS709TP has built- in PoE support on all eight 10/100 interfaces. With a Gigabit Ethernet port typically used to connect the wireless controller to the network backbone, WFS709TP supports advanced security features such as 802.1x, EAP-PEAP, EAP-TLS, EAP-TTLS, 802.11i, MAC address, SSID and location-based authentication.
With identity-based security features such as support for RADIUS and AAA server support, NETGEAR ProSafe Smart Wireless Controller, truly unifies wired and wireless access without compromising on security.
Deployment
Deployed as an overlay on the existing network infrastructure, WFS709TP centrally manages, deploys, monitors and controls your wireless infrastructure. Supporting multiple deployment architectures including standalone wireless controller deployments to hierarchical setups in master/local configurations, the NETGEAR ProSafe Smart Wireless Controller, can be configured in “master” mode where all the configuration and security parameters are managed for the entire wireless network. In addition, WFS709TP can be configured in “local” mode, acting as policy enforcement points for the “master” controller as part of a hierarchical setup.
The overall Smart Wireless Controller solution supports up to 32 access points with the Smart Wireless Controllers configured in redundant master/local mode and up to 48 access points with the Smart Wireless Controllers configured in non-redundant master/local configuration. A standalone Smart Wireless Controller supports up to 16 access points.
IntelliFi RF Management
Targeted towards the growing business NETGEAR ProSafe Smart Wireless Controller provides continuous wireless coverage with features such as IntelliFi radio management. IntelliFi radio management provides automatic self-configuration of all radio parameters including transmit power level, channel, load balancing and interference avoidance.
For low-latency applications such as VoIP, NETGEAR ProSafe Wireless Controller delivers VoIP over wireless by providing support for call admission control, voice-aware fast-roaming and strict over-the-air QoS to deliver mobile voice capabilities.
Access Points
Wireless users on the network can now experience seamless roaming as moving between multiple access points is made simple with the ProSafe Smart Wireless Controller centralized architecture. All user states, including security and mobility information, are maintained in the centralized Smart Wireless Controller. Access points (AP’s) act as logical extensions to the WFS709TP, accepting wireless traffic and sending it to the Wireless Controller over IP tunnels.
Access points supported include NETGEAR ProSafe 802.11a/g Dual Band Light Wireless Access Point (WAGL102) and NETGEAR ProSafe 802.11g Light Wireless Access Point (WGL102).
The WFS709TP can also manage existing NETGEAR WG102 and WAG102 Wireless Access Point deployment by a one-time image download available on http://support.netgear.com that allows the existing wireless access point to be managed by the Wireless Controller.
RF Planning Tool
With integrated RF planning tools, administrators can input floor plan images, number of floors, building dimensions, desired coverage and an overlap factor for fault tolerance. The planning tools compute the predicted RF characteristics of the building, plot the optimal location of the access points and display predicted coverage.
Guest Access and Redundancy
Guest access, provided by a built-in captive portal, allows guest users connecting over the wireless network restricted guest level access to the network, prohibiting them any access to the sensitive data on the corporate network.
For mission-critical applications requiring network resiliency, the WFS709TP supports fault tolerant hardware with industry standard N+1 wireless controller redundancy and access point interleaving for access point redundancy. These features make it possible to provide a wireless network with no single point of failure, guaranteeing the highest possible availability.
Wednesday, June 3, 2009
How Wifi Network Works

A Wi-Fi enabled device such as a PC, game console, mobile phone, MP3 player or PDA can connect to the Internet when within range of a wireless network connected to the Internet. The coverage of one or more interconnected access points — called a hotspot — can comprise an area as small as a single room with wireless-opaque walls or as large as many square miles covered by overlapping access points. Wi-Fi technology has served to set up mesh networks, for example, in London. Both architectures can operate in community networks.
In addition to restricted use in homes and offices, Wi-Fi can make access publicly available at Wi-Fi hotspots provided either free of charge or to subscribers to various providers. Organizations and businesses such as airports, hotels and restaurants often provide free hotspots to attract or assist clients. Enthusiasts or authorities who wish to provide services or even to promote business in a given area sometimes provide free Wi-Fi access. There are already more than 300 metropolitan-wide Wi-Fi (Muni-Fi) projects in progress. There were 879 Wi-Fi based Wireless Internet service providers in the Czech Republic as of May 2008.
Wi-Fi also allows connectivity in peer-to-peer (wireless ad-hoc network) mode, which enables devices to connect directly with each other. This connectivity mode can prove useful in consumer electronics and gaming applications. When wireless networking technology first entered the market many problems ensued for consumers who could not rely on products from different vendors working together. The Wi-Fi Alliance began as a community to solve this issue — aiming to address the needs of the end-user and to allow the technology to mature. The Alliance created the branding Wi-Fi CERTIFIED to reassure consumers that products will interoperate with other products displaying the same branding.
Many consumer devices use Wi-Fi. Amongst others, personal computers can network to each other and connect to the Internet, mobile computers can connect to the Internet from any Wi-Fi hotspot, and digital cameras can transfer images wirelessly. Routers which incorporate a DSL-modem or a cable-modem and a Wi-Fi access point, often set up in homes and other premises, provide Internet-access and internetworking to all devices connected (wirelessly or by cable) to them. One can also connect Wi-Fi devices in ad-hoc mode for client-to-client connections without a router. Wi-Fi also enables places which would traditionally not have network to be connected, for example bathrooms, kitchens and garden sheds. The "father of Wi-Fi", Vic Hayes, stated that being able to access the internet whilst answering a call of nature was "one of life's most liberating experiences".
As of 2007 Wi-Fi technology had spread widely within business and industrial sites. In business environments, just like other environments, increasing the number of Wi-Fi access-points provides redundancy, support for fast roaming and increased overall network-capacity by using more channels or by defining smaller cells. Wi-Fi enables wireless voice-applications (VoWLAN or WVOIP). Over the years, Wi-Fi implementations have moved toward "thin" access-points, with more of the network intelligence housed in a centralized network appliance, relegating individual access-points to the role of mere "dumb" radios. Outdoor applications may utilize true mesh topologies. As of 2007 Wi-Fi installations can provide a secure computer networking gateway, firewall, DHCP server, intrusion detection system, and other functions.
 Image via Wikipedia
Image via Wikipedia
In addition to restricted use in homes and offices, Wi-Fi can make access publicly available at Wi-Fi hotspots provided either free of charge or to subscribers to various providers. Organizations and businesses such as airports, hotels and restaurants often provide free hotspots to attract or assist clients. Enthusiasts or authorities who wish to provide services or even to promote business in a given area sometimes provide free Wi-Fi access. There are already more than 300 metropolitan-wide Wi-Fi (Muni-Fi) projects in progress. There were 879 Wi-Fi based Wireless Internet service providers in the Czech Republic as of May 2008.
Wi-Fi also allows connectivity in peer-to-peer (wireless ad-hoc network) mode, which enables devices to connect directly with each other. This connectivity mode can prove useful in consumer electronics and gaming applications. When wireless networking technology first entered the market many problems ensued for consumers who could not rely on products from different vendors working together. The Wi-Fi Alliance began as a community to solve this issue — aiming to address the needs of the end-user and to allow the technology to mature. The Alliance created the branding Wi-Fi CERTIFIED to reassure consumers that products will interoperate with other products displaying the same branding.
Many consumer devices use Wi-Fi. Amongst others, personal computers can network to each other and connect to the Internet, mobile computers can connect to the Internet from any Wi-Fi hotspot, and digital cameras can transfer images wirelessly. Routers which incorporate a DSL-modem or a cable-modem and a Wi-Fi access point, often set up in homes and other premises, provide Internet-access and internetworking to all devices connected (wirelessly or by cable) to them. One can also connect Wi-Fi devices in ad-hoc mode for client-to-client connections without a router. Wi-Fi also enables places which would traditionally not have network to be connected, for example bathrooms, kitchens and garden sheds. The "father of Wi-Fi", Vic Hayes, stated that being able to access the internet whilst answering a call of nature was "one of life's most liberating experiences".
As of 2007 Wi-Fi technology had spread widely within business and industrial sites. In business environments, just like other environments, increasing the number of Wi-Fi access-points provides redundancy, support for fast roaming and increased overall network-capacity by using more channels or by defining smaller cells. Wi-Fi enables wireless voice-applications (VoWLAN or WVOIP). Over the years, Wi-Fi implementations have moved toward "thin" access-points, with more of the network intelligence housed in a centralized network appliance, relegating individual access-points to the role of mere "dumb" radios. Outdoor applications may utilize true mesh topologies. As of 2007 Wi-Fi installations can provide a secure computer networking gateway, firewall, DHCP server, intrusion detection system, and other functions.
Tuesday, May 26, 2009
Securing your wireless network
 Image via Wikipedia
Image via Wikipedia
Wireless network security should be your first priority as your setting up a router. An unsecured wireless network is an open invitation to trouble. Your neighbors, nearby businesses, even a stranger parked out in the street can access your network if it’s not secured. Wireless Networking Security Basics
Securing your wireless network is easy with these tips:
• Don’t leave defaults. Your router or access point is set up via a Web page that connects directly to the device. If you haven’t done so already, change the administration username and password. Hackers that know the login defaults will have an easy time configuring your network to be an open book.
• Get cryptic. Wireless network equipment can scramble the data that passes between computers on the network. Make sure to turn on the strongest encryption that all of your computers will support. It is crucial that all computers use the same type of encryption, or they won’t be able to communicate with each other. WPA and WEP are common encryption standards.
• Be picky. All network cards and hardware have unique identifiers called MAC addresses. Your router can be configured to only allow access to certain MAC addresses through a function called MAC Address Filtering. Turn this on and input the MAC addresses of all the network devices (cards, access points, etc.) that should have access to your wireless network.
To find the MAC address of your wireless card, use the following procedure:
◦ From the Windows Start menu, select Run
◦ Type in the command cmd and press return
◦ In the new window, enter the command ipconfig /all
◦ The MAC address (sometimes called the physical address) will be listed as a series of letters and number in the form—XX-XX-XX-XX-XX-XX
◦ Record the MAC address and close the window
◦ Note: you can add the MAC address of visiting PCs, but don’t forget to remove them from you filter list later.
• Wall yourself in. Make sure that firewall wireless network security software is enabled on all computers and routers in the network. Firewall software is designed to block unauthorized access to hardware. This is added level of security is a simple step toward a more secure network
Monday, May 25, 2009
Extending The Range Of Wireless Networks

Although a wireless transmitter is limited in its range, wireless extension points can be installed to boost its signal and make the range of the network much larger. These wireless extension points are commonly known as repeaters.
Several companies have started to manufacture wireless repeaters, despite the fact that these devices are not part of the wireless standard. Wireless repeaters are designed to resolve certain problems with wireless coverage. The further away you are from where the wireless signal originates, the weaker the signal becomes. Eventually, you can't receive the signal at all, regardless of what equipment you have. The problem is sometimes addressed by running wires out as far as the network coverage is desired, and then have it 'break out' into wireless every now and then using a wireless access point. This is generally more trouble than it is worth, since the idea behind a wireless network is to avoid installing wires! Wireless repeaters resolve the problem in a much better way.
Wireless repeaters work as a relay, taking existing wireless signals and making them stronger. This makes the range of a signal bigger each time. If the repeaters are placed correctly, you can move computers a considerable distance from the wired portion of the network, the router or access point, for example, without failure. The single requirement of this arrangement is that the extension points must overlap; a repeater can't repeat signals that it doesn't receive. Since wireless networking signals are essentially radio signals, repeaters take all the radio signals they receive on a specific frequency and use their power to amplify the signals and rebroadcast them. The signal is not degraded in this process, so it can be repeated as many time as required.
Theoretically, wireless repeaters could be placed in a line for several miles, extending the network out that far, and because these extension points don't need complicated computer technology to operate, they are much cheaper than routers or access points. Some companies combine repeaters and direction antennas to link to LANs that are several miles apart. This is a cheaper method than worrying about connecting over the Internet or installing their own underground lines. In the future, repeater technology could create wireless networks that cover entire cities.
As a consumer, you are currently limited to getting your repeater from large manufacturing firms such as Linksys and D-Link. These companies call their repeaters by different names, including Linksys' Range Expander and D-Link's Range Extender. There are several issues to consider when buying a wireless extension point. The most important is to make sure that it is compatible with the equipment you have. Because there is no standard for wireless extension points, you're better off staying with the same company that makes the rest of your equipment or at least investigate whether any new equipment will work with your system. You should also find out whether an extension point has any Ethernet ports. While it isn't necessary that this is included, it is useful if you want to connect the extension to a wired network. This issue arises basically if you want to connect two LANs in a wireless manner.
How to Secure Your Wireless Network Connection
If you
 subscribe to DSL or cable internet service the chances are good that you are using a wireless router. How secure is your wireless router? I will explain in this article what steps to you need to take to insure that you have the most secure home network that's possible. Have you ever gone to "My Network Places" in Windows and viewed all your neighbors' wireless network connections? You will notice that some say secure and some say unsecure. Well you want to make sure that yours' says secure. This is the first step in securing your wireless network connection.
subscribe to DSL or cable internet service the chances are good that you are using a wireless router. How secure is your wireless router? I will explain in this article what steps to you need to take to insure that you have the most secure home network that's possible. Have you ever gone to "My Network Places" in Windows and viewed all your neighbors' wireless network connections? You will notice that some say secure and some say unsecure. Well you want to make sure that yours' says secure. This is the first step in securing your wireless network connection.Your first line of defensive is your wireless routers' data encryption. Basically your router takes your data and encodes it so that no one else can intercept your data. Usually the manufactures' default encryption setting is set to off.
The first thing to do is to log into your wireless router (see instruction guide for your router) and go to wireless settings and turn on encryption. There are two forms of encryption WEP which is older and easy to crack and WPA which is the more secure encryption. If your router has a WPA2 encryption then use this one as it is the most recent version. Always use a strong password for your encryption key. A combination of upper and lower case letters and numbers will do the job nicely.
As an added security precaution always use your router's built in firewall. Refer to your router owner's manual on the various settings that are offered. What a firewall will do is prevent any unauthorized internet hackers from accessing your pc. As an added precaution you can also add a software base firewall which will offer many advance settings that may not be found in your router's firewall.
As an added precaution whenever you are not using your computer you can disconnect from the internet by right clicking on windows network icon connection in the bottom right of your task bar and select disable. If you have firewall software installed on your pc, your software will have a similar feature.
One more topic I want to cover and that is public Wi-Fi Hotspots.
Whenever you are in a public area like an airport, bus terminal, public library or any place where there may be a Wi-Fi Hotspot you need to take some precautions.
Make sure that your pc's software firewall is turned on and that your windows file sharing is turned off.
Never use the internet to log into your bank account or any other service that requires the use of passwords. You need to take this precaution to make sure your Wi-Fi connection is not being monitored to record your keystrokes.
Always turn off your Wi-Fi radio when you are not at a Wi-Fi hotspot. This will prevent hackers from using your pc to create a peer-to-peer Wi-Fi connection and accessing it directly.If you follow these few simple steps you will have a much more secure pc connection and less of a chance of being hacked into and having personal information stolen. As always nothing is 100% secured but these steps will give you much better security than what you had.
The Advantages Of Wireless Networks
 In this world of modern technology, most people prefer not to connect computers with Ethernet cables because excessive cables scattered throughout their office or home is unsightly. You can choose to install a wireless network to avoid excessive cabling. For a wireless network, there is no need to use Ethernet cables to connect your computers to the DSL or router.
In this world of modern technology, most people prefer not to connect computers with Ethernet cables because excessive cables scattered throughout their office or home is unsightly. You can choose to install a wireless network to avoid excessive cabling. For a wireless network, there is no need to use Ethernet cables to connect your computers to the DSL or router.Usually, a wireless network broadcast signal uses one or more wireless routers or wireless access points. The access points or router are provided with an aerial and an Ethernet port. The Ethernet port in the access point must be connected to the modem which is provided by your internet service provider, if you need internet access. If you have to move the wireless network to another place, you can simply transfer and install it in your new location easily.
You can also make a combination of wired and wireless connections with an access point or wireless router. The access point functions as the receiver and radio frequency transmitter and can interact with computers, IP Phones, PDAs and other access points having 802.11 wireless adapters. IEEE 802.11 standard of wireless transmission is utilized in a wireless local area network (WLAN). Certain other wireless networking standards such as Bluetooth are available now. However, 802.11 standard is considered as the most effectual networking solution. Actually, the aim of the developers of this network interface was to connect computers through a local area network. However, it has now been changed and a wireless network interface is also used for Voice over Internet Protocol (VoIP) and internet access.
Based on the surveys conducted so far, it is clear that you can stay connected in your network for a long period each day. If you have a laptop with a wireless connection, you can walk around your office with your laptop without losing the connection. Nowadays, certain emergency services are transferring their confidential data through a wireless network. We can consider this as an evidence for the data security which is provided by wireless network. You can send and share data quickly through a wireless network. This is the main reason why businesses and people prefer this network interface for their data sharing. Another important fact regarding wireless networks is that you can connect to the network easily even from the regions which have poor telecom infrastructure.
Some of the main reasons which make the wireless network interface popular include:
i) Convenience as you can use this network interface at home, the office or anywhere else without hassle.
ii) WLANs are available anywhere in the world at an affordable cost.
iii) If you are moving to a new location, you can transfer the interface and install it at your new location easily.
iv) There is no need for an Ethernet cable to connect computers to each other.
For a business, one of the main advantages in setting up a wireless network is savings. You can access the changes in your business in a short period of time after installing the wireless network. There is no need to spend money on cables and other equipments. The cost of maintaining a wireless network is also less when compared to other network interfaces.
Nowadays, you can buy wireless routers at an affordable cost. Also having a wireless network can increase productivity and improve the working environment in your office.
One of the main drawbacks of this network interface is that it may cause health and environmental hazards. Recent researches reported that the constant use of wireless network interfaces may lead to memory loss, poor concentration, premature senility, nausea and even the hazardous disease named cancer. Some environmental hazards that may occur due the constant usage of this interface are also reported. These hazards occur due to electromagnetic radiation coming out of wireless networks.
How to Optimize Your Wireless Network Channel

When you use a wireless network at home, range and performance can be influenced by a lot of factors. The location of your wireless router as well as the location of your PC and/or laptop can make a lot of difference. Concrete walls also have a strong influence on Wi-Fi signals, so too many concrete walls in between the communication devices will reduce the signal strength, and as a result, the performance. But range and obstacles are not the only possible problems with wireless networks. What about your neighbors? If they are using a wireless network, chances are, you are both using the same frequency, which would cause interference and again loss of signal quality. Since wireless internet access is so common these days, it's better to check that too.
Here's How You Can Improve Your Wi-Fi Network! Depending on the location of your equipment, you can try to change the direction of your antennas. If your router has a built-in antenna, consider hanging it on a wall instead of placing it horizontally on a cabinet to change antenna direction. Most routers will come with instructions on best positioning for maximum range. If you want to further optimize the range and performance of your wireless network, you might need to change the frequency of your WiFi communication. There is a dedicated bandwidth for WiFi networks, in which multiple channels are defined. The problem is that many vendors configure their hardware to use a default channel. Typically this is channel 6, since it is the middle of the range (1 to 11 in the US, up to 13 for Europe).
To find out if you need to change your wireless network frequency, you need to know what channel you are using and if the other channels are better. There are many tools available for this, and one of them is called NetStumbler. The current version is 0.4. The program can be installed with the default options. Once you start the application, it will automatically start a scan of the wireless networks in your surroundings. In the results pane, you can see all detected networks grouped by MAC address, SSID or channel. The colored icon in front of the MAC address indicates the signal strength. Using these details, you can first check how many networks are using the same channel as you are. You will need to know your SSID of course (either printed at the bottom of your wireless router, if it came from your ISP, or check the network settings on your computer's wireless card).
Ideally, there should not be (too) many wireless networks on the same channel, but if there are, you want to make sure they have low signal strength. If there are too many wireless networks on the same channel, try changing the channel to improve your wireless network range and performance. This needs to be done in the wireless router or access point. The hardware will come with instructions on how to change the WiFi channel. Your laptop or PC's wireless card will automatically switch to the new channel. If you are using a laptop, you can also use the program to see where your signal strength is best. Move around with the laptop and see which location in your house has the best signal strength. You can use the colored icon as well as the 'signal' columns to assess the network quality. Make sure the network scanning is active to ensure the values are updated while you move around.
Using these Wi-Fi tips, you can easily improve your wireless internet access speed, or solve problems with your wireless internet connection.
Here's How You Can Improve Your Wi-Fi Network! Depending on the location of your equipment, you can try to change the direction of your antennas. If your router has a built-in antenna, consider hanging it on a wall instead of placing it horizontally on a cabinet to change antenna direction. Most routers will come with instructions on best positioning for maximum range. If you want to further optimize the range and performance of your wireless network, you might need to change the frequency of your WiFi communication. There is a dedicated bandwidth for WiFi networks, in which multiple channels are defined. The problem is that many vendors configure their hardware to use a default channel. Typically this is channel 6, since it is the middle of the range (1 to 11 in the US, up to 13 for Europe).
To find out if you need to change your wireless network frequency, you need to know what channel you are using and if the other channels are better. There are many tools available for this, and one of them is called NetStumbler. The current version is 0.4. The program can be installed with the default options. Once you start the application, it will automatically start a scan of the wireless networks in your surroundings. In the results pane, you can see all detected networks grouped by MAC address, SSID or channel. The colored icon in front of the MAC address indicates the signal strength. Using these details, you can first check how many networks are using the same channel as you are. You will need to know your SSID of course (either printed at the bottom of your wireless router, if it came from your ISP, or check the network settings on your computer's wireless card).
Ideally, there should not be (too) many wireless networks on the same channel, but if there are, you want to make sure they have low signal strength. If there are too many wireless networks on the same channel, try changing the channel to improve your wireless network range and performance. This needs to be done in the wireless router or access point. The hardware will come with instructions on how to change the WiFi channel. Your laptop or PC's wireless card will automatically switch to the new channel. If you are using a laptop, you can also use the program to see where your signal strength is best. Move around with the laptop and see which location in your house has the best signal strength. You can use the colored icon as well as the 'signal' columns to assess the network quality. Make sure the network scanning is active to ensure the values are updated while you move around.
Using these Wi-Fi tips, you can easily improve your wireless internet access speed, or solve problems with your wireless internet connection.
How To Create A Wireless Computer Network

While living in a growing age of technology, having at least one computer in the home is just as common as having a refrigerator. Most homes today will have some sort of computer equipment for either personal use or business use. With today's wireless-equipped laptops, a wireless router and, if you need one, a wireless adapter card, even the technically-challenged can create a network in a heartbeat. This discussion isn't about Bluetooth technology, nor does it relate to Macs.
The First StepWorkstations, printers, and laptops need a wireless adapter card installed. They're easy to install--sometimes they're already built in. If so, your equipment will say it's wireless network capable. If not, remove the case from your desktop computer, follow the adapter card's directions, and you'll easily identify the slot the card fits into. On a laptop, the card slot is on one of the outside edges of the keyboard half. The card only fits in one way and installs in two seconds, no problem. Once the adapter is set into its slot, Windows' setup wizard steps you through installing the driver. You'll get the familiar message, "Windows found new hardware." Follow the prompts. The current wireless protocol is 802.11. Wireless cards costs between $20 and $130. They can be found at any computer store or online outlet. The $20 card should be adequate. For a few dollars, weak-kneed users can get a pro to install the card and drivers.
Buying Your Wireless Router Going in search of wireless routers at an office supply megastore, you'll find them from $39 and up. They come with 4 Ethernet ports plus a wireless access point. The Ethernet ports are sockets for setting up a "wired" network, but since you're going wireless, you won't use them. The wireless access point is the sort of radio thing on the router that talks to your computer to make the wireless connection. It doesn't require you to plug anything in. Spending extra money buys more speed between router and computer, but for home use, on a small network, it's not really relevant. Usually, a router that transfers data at 100 megabits per second is fast enough. The package will tell you the speed.
Safeguard Your Stuff By the way, an important fact about wireless routers is that they act as "firewalls." A firewall is software or hardware that prevents hackers from hacking into your system. The router puts an extra layer of security between you and them. Some people claim the protection is negligible but a techie friend of this writer, with every piece of security known to man, tried to hack my network to demonstrate how feeble the router's protection was. He said, "In 10 minutes, I'll have your data." Three hours later, cussing a blue streak, he threw in the towel. Good security.
Wireless - Continued To install the router, rely on manufacturer's directions. All routers are slightly different. For example, you'll plug your basic Netgear router into an electrical outlet, go back to your computer and navigate to Control Panel -- Network Connections. The wireless network connection icon should say you have succeeded and are connected. Your router is now talking to your computer. That's it. Next, choose enable encryption, which is a way to assigning a security key, like a password, to the network's access to keep neighbors or anyone else from using your network. Gurus encourage everyone to do this. It's not difficult to figure out. The manual directs you to type 192.168.0.1 into the address bar of Internet Explorer. Every user manual has a similar IP address (Web address) to an administrative program for each router. It's easy to follow menu selections on the page that comes us next. The help files are generally user-friendly and tech support is available by phone as well.
Hooking Up With your new network set up, you add security cameras, printers, shared storage or anything else that can accept an adapter card or comes with network capability. Each item added -- printer, camera, computer -- needs wireless capability or a card and each shows up on the network with a name you give it - like, "new photo printer" or "Joe's laptop." The best part of the whole set up is that the wireless signal goes through most walls, allowing you to work almost anywhere in your home, sans the yards of black spaghetti that used to connect you. Take your laptop n front of the fireplace. Recliner chair becomes your desk. Sip some hot buttered rum and be the envy of the neighborhood.
Sunday, May 17, 2009
Wireless Network Security Setup Guide
Just a few years ago I was clueless about why I should secure my wireless network. I didn’t care if other people used my wireless signal to surf the internet, and I thought it was too much hassle to figure out how to encrypt my network. What I didn’t realize, is that computer criminals rely on people like me to carry out their crimes. All they had to do was sit outside of my house and run some nifty software while they collected all of my personal data and all that it cost them was gas and time. It took me getting my credit card number stolen and my credit rating destroyed before I finally decided to take network security and the security of my data seriously. I hope this story isn’t too familiar to any of you out there but if it is I have just the guide for you.
Recently I was asked by the wonderful staff here at TechwareLabs to write a little guide on securing your home network, and explain a little bit of the techno-babble associated with network security encryption. I hope this guide finds you well and saves you from the mistakes so many like myself make. We will make this guide as easy to understand as possible so that everyone from the novice to the expert can tighten down the latches on their home and business security.
If you don’t think you have the time to secure your network all you have to remember is that it only takes one penetration of your data to cost you anywhere from hundreds to thousands of dollars. Getting ready to contact your credit card companies and maybe even a lawyer to start rebuilding your credit. We hope you aren’t planning on buying anything on credit any time soon.
First, let’s take a look at the most common hardware that consumers use to create wireless networks for their homes and small businesses. Knowing what you have is the first step to locking down unauthorized access.
Recently I was asked by the wonderful staff here at TechwareLabs to write a little guide on securing your home network, and explain a little bit of the techno-babble associated with network security encryption. I hope this guide finds you well and saves you from the mistakes so many like myself make. We will make this guide as easy to understand as possible so that everyone from the novice to the expert can tighten down the latches on their home and business security.
If you don’t think you have the time to secure your network all you have to remember is that it only takes one penetration of your data to cost you anywhere from hundreds to thousands of dollars. Getting ready to contact your credit card companies and maybe even a lawyer to start rebuilding your credit. We hope you aren’t planning on buying anything on credit any time soon.
First, let’s take a look at the most common hardware that consumers use to create wireless networks for their homes and small businesses. Knowing what you have is the first step to locking down unauthorized access.
Subscribe to:
Posts (Atom)


![Reblog this post [with Zemanta]](http://img.zemanta.com/reblog_e.png?x-id=98624ae0-cf69-4d15-98c4-5344ff4e353e)
![Reblog this post [with Zemanta]](http://img.zemanta.com/reblog_e.png?x-id=b7bb7ef4-d5fe-4396-98ca-55999ea9d2bb)
![Reblog this post [with Zemanta]](http://img.zemanta.com/reblog_e.png?x-id=97772b14-fac8-4ed5-b869-674a89436fa1)
![Reblog this post [with Zemanta]](http://img.zemanta.com/reblog_e.png?x-id=cf7b6775-575e-421c-9ac8-8f758c554d4f)
![Reblog this post [with Zemanta]](http://img.zemanta.com/reblog_e.png?x-id=6d8a528d-8a57-444a-a607-225d6cd6dd2e)
![Reblog this post [with Zemanta]](http://img.zemanta.com/reblog_e.png?x-id=e11ece4c-7c77-45a3-9f7e-ec7eed65071e)
![Reblog this post [with Zemanta]](http://img.zemanta.com/reblog_e.png?x-id=fe80c770-63af-45f7-b2e9-71c481e08451)
![Reblog this post [with Zemanta]](http://img.zemanta.com/reblog_e.png?x-id=97685e46-8352-463b-8792-ba7a90e28b84)
![Reblog this post [with Zemanta]](http://img.zemanta.com/reblog_e.png?x-id=a0f2a7d2-cca4-4d89-8481-518520b8647c)
![Reblog this post [with Zemanta]](http://img.zemanta.com/reblog_e.png?x-id=86f39c81-de3c-4c8c-95e2-a975cda424c6)






